- cross-posted to:
- technology@lemmy.world
- cross-posted to:
- technology@lemmy.world
Damn… I guess the next idea is going offline for good
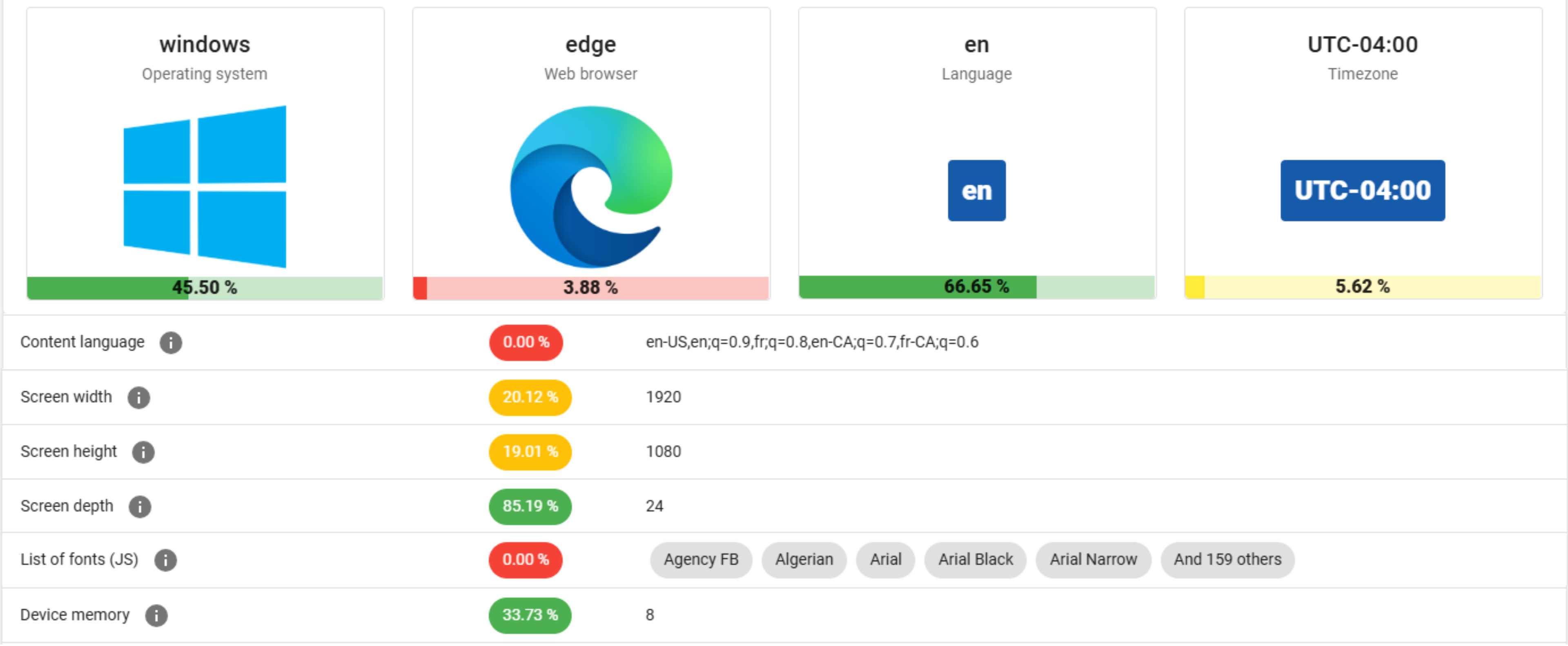
This is a bit of a misnomer. No one PC can be fully anonymized or fully private, even if the PC provided fake data points, they will still be technically fingerprinted. Having said that, having a browser that tries to spoof stuff like LibreWolf, Tor or IronFox is decent.
The gains in using a VPN, among other best practices is that helps --assuming people do not log on to something like Google-- is to minimize the fingerprint of the PC to you, as a user. Assuming one trust their VPN provider, helps.
Tor leverages the point of having all users look and be fingerprinted mostly as the same, so you get lost in the shuffle and crowd.
Ultimately being truly anonymous on the internet is pretty hard, and thus VPNs are mostly helpful for getting around region blocks for streaming services, not for obtaining more privacy.
I disagree.
There seems to constantly be two sides of the privacy discussion with public VPN options and they’re both wrong on their own. It’s correct that using a VPN on its own is not enough to keep you private online, fingerprinting being one example to why. However, not using a VPN but having no identifiable browser fingerprint doesn’t either, since your IP is still a fingerprint too.
I like to give the following analogies:
- Doing only an oil change on your vehicle but no other maintenance won’t keep your vehicle running forever
- Doing all vehicle maintenances except oil changes won’t keep your vehicle running forever
If the goal is to be private, remember that a VPN is only one tool in a very large tool belt.
I think TOR would be more suitable than a VPN
Tor is definitely another option. For my personal use however, I have my entire network covered by a VPN so all outgoing traffic uses it.
I’m sure I could setup Tor to do the same, but I imagine my family and I would get blocked more heavily on sites, as well as get our bank accounts and such flagged or something.
Like many things, it obviously depends on your threat model.
They do more then fingerpring your browser.
no shit
I use VPN because of the ISP and the network, not to become anonymous to the websites I visit.
But VPNs aren’t supposed to make you anonymous.
They secure your data while in transit to/from the exit node. Maybe that’s your job so you can access their LAN. Or it’s a public VPN that secures your dada from the local WiFi or ISP you’re directly connected to. That’s all it’s built for.And what do you thing HTTPS does exactly? Whe the web was HTTP sure VPN’s had a point as people on public wifi could sniff your trafic. Now they can’t.
It only encrypts the data within the HTTPS packet. But where that packet is going is still transparent.
It also doesn’t do anything for non web traffic. Email through SMTP or IMAP, FTP, lots of things don’t use HTTP at all.
Doesn’t browser with anti-fingerpriting give the same settings to everyone using that browser so they all look like the same person?
Yes and I think that’s kinda dumb. It’s never going to be possible to have everyone look the same. I would go the other route. Randomize everything everytime so you never leave twice the same fingerprints. That’s way easier and it polutes marketers dabases, which is a double win.
Back in the day there were apps that generated phony web searches to obfuscate your real searches. Seems like there could be tools to mess around and change browser fingerprints periodically. No?
Already done, see: https://github.com/uazo/cromite
When I go to the fingerprint test, a bunch of the values like canvas resolution and timezone are randomized.
…Not everything, though.
It could be done on the browser level (maybe it’s something browsers like LibreWolf do), however, it would break sites that require the fingerprints to be the same for “security reasons” which may or may not be a legitimate claim.
You could say “well, I’m not going to use that particular website then”, but the problem is that there are less and less websites that don’t require these technologies to function properly.
There is a browser extension called Chameleon that will spoof a fair amount of data, but after testing it against one of those fingerprint test sites, it looks like it doesn’t/can’t spoof everything.